The Human Layer For
The New Internet
The Human Layer For The New Internet
The Human Layer For
The New Internet
Simplifying Compliance by Proving Humanity
while Maintaining Privacy
Simplifying Compliance by
Proving Humanity While
Maintaining Privacy
Simplifying Compliance by Proving Humanity
while Maintaining Privacy
Testnet Live Now
Testnet Live Now
Testnet Live Now
500k +
Verified Users
1M +
VCs Issued
1.2M +
DIDs Issued
500k +
Verified Users
1M +
VCs Issued
1.2M +
DIDs Issued
500k +
Verified Users
1M +
VC Issued
1.2M +
DIDs Issued
500k +
Verified Users
1M +
VC Issued
1.2M +
DIDs Issued
500k +
Verified Users
1M +
VC Issued
1.2M +
DIDs Issued
500k +
Verified Users
1M +
VC Issued
1.2M +
DIDs Issued
ADDRESSING CHALLENGES
ADDRESSING CHALLENGES
ADDRESSING CHALLENGES

$50 Billion in fines for Non-Compliance
Difficult for Web3 businesses to adopt to rapidly evolving compliance, exposing them to penalties levied by regulators

$50 Billion in fines for Non-Compliance
Difficult for Web3 businesses to adopt to rapidly evolving compliance, exposing them to penalties levied by regulators

$50 Billion in fines for Non-Compliance
Difficult for Web3 businesses to adopt to rapidly evolving compliance, exposing them to penalties levied by regulators

$50 Billion in fines for Non-Compliance
Difficult for Web3 businesses to adopt to rapidly evolving compliance, exposing them to penalties levied by regulators

70% of Online Users are victims to ID Theft
Most online users are vulnerable to ID theft, data leaks, friction while accessing services, and lack of control over their personal data.

70% of Online Users are victims to ID Theft
Most online users are vulnerable to ID theft, data leaks, friction while accessing services, and lack of control over their personal data.

70% of Online Users are victims to ID Theft
Most online users are vulnerable to ID theft, data leaks, friction while accessing services, and lack of control over their personal data.

70% of Online Users are victims to ID Theft
Most online users are vulnerable to ID theft and data leaks along with friction while accessing services and no control over their personal data

$4.4 Million - Cost to recover from a data breach
Globally businesses experience massive losses in all aspects, when they fail to protect users and their data from hacks, breaches and leaks.

$4.4 Million - Cost to recover from a data breach
Globally businesses experience massive losses in all aspects, when they fail to protect users and their data from hacks, breaches and leaks.

$4.4 Million - Cost to recover from a data breach
Globally businesses experience massive losses in all aspects, when they fail to protect users and their data from hacks, breaches and leaks.

$4.4 Million - Cost to recover from a data breach
Globally businesses experience massive losses in all aspects, when they fail to protect users and their data from hacks, breaches and leaks.
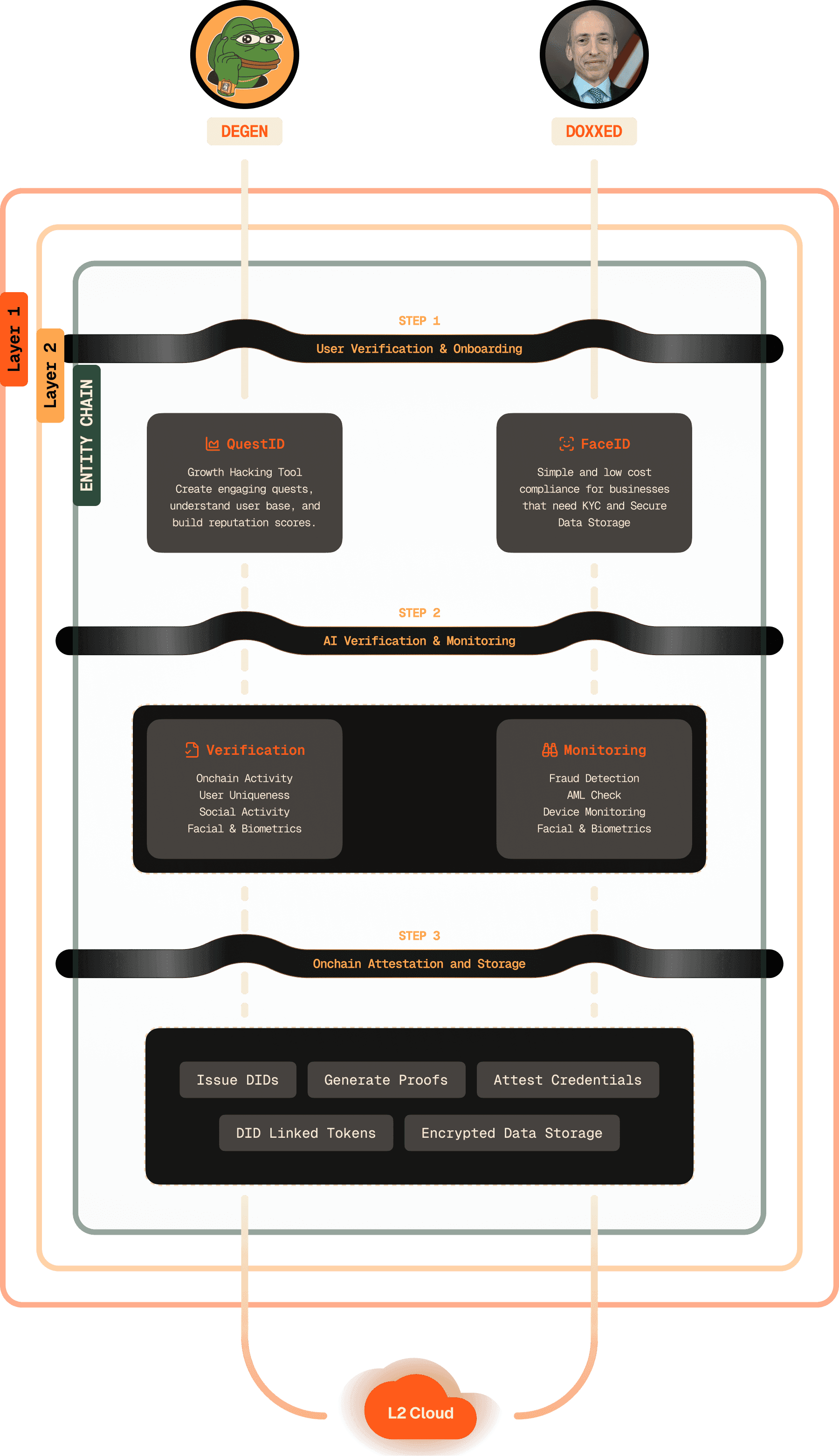
Entity Protocol enables businesses to verify their users and comply with regulation in a simple, secure and low cost manner while empowering users to take control of their data.
Entity Protocol enables businesses to verify their users and comply with regulation in a simple, secure and low cost manner while empowering users to take control of their data.
Entity Protocol enables businesses to verify their users and comply with regulation in a simple, secure and low cost manner while empowering users to take control of their data.
PLUG & PLAY COMPLIANCE
PLUG & PLAY COMPLIANCE



Entity protocol ensures user privacy along with compliance with the rapidly evolving regulatory landscape
Entity protocol ensures user privacy along with compliance with the rapidly evolving regulatory landscape
Entity protocol ensures user privacy along with compliance with the rapidly evolving regulatory landscape
ON BOARDING VERIFIED USERS
Collaborating with industry leaders to build a secure and efficient digital identity ecosystem
TECHNOLOGY STACK
TECHNOLOGY STACK
Cutting-edge solutions powering secure and efficient digital identity management

AI Verification
Cutting edge, AI Powered Security & ID Verification tools to ensure Compliance and Privacy

AI Verification
Cutting edge, AI Powered Security & ID Verification tools to ensure Compliance and Privacy

AI Verification
Cutting edge, AI Powered Security & ID Verification tools to ensure Compliance and Privacy

AI Verification
Cutting edge, AI Powered Security & ID Verification tools to ensure Compliance and Privacy

Zero Knowledge Proofs
Prove your identity and other attributes without actually revealing the data to anyone

Zero Knowledge Proofs
Prove your identity and other attributes without actually revealing the data to anyone

Zero Knowledge Proofs
Prove your identity and other attributes without actually revealing the data to anyone

Zero Knowledge Proofs
Prove your identity and other attributes without actually revealing the data to anyone

Tokenized Data
Share your data in the most secure way through PoPs, SBTs, NFTs, Ordinals, VCs, and more.

Tokenized Data
Share your data in the most secure way through PoPs, SBTs, NFTs, Ordinals, VCs, and more.

Tokenized Data
Share your data in the most secure way through PoPs, SBTs, NFTs, Ordinals, VCs, and more.

Tokenized Data
Share your data in the most secure way through PoPs, SBTs, NFTs, Ordinals, VCs, and more.

Credential Attestation
Protect the integrity and authenticity of user data without relying on 3rd parties

Credential Attestation
Protect the integrity and authenticity of user data without relying on 3rd parties

Credential Attestation
Protect the integrity and authenticity of user data without relying on 3rd parties

Credential Attestation
Protect the integrity and authenticity of user data without relying on 3rd parties

Key Management
Frictionless access to web3 environments without the need for wallets and mnemonics

Key Management
Frictionless access to web3 environments without the need for wallets and mnemonics

Key Management
Frictionless access to web3 environments without the need for wallets and mnemonics

Key Management
Frictionless access to web3 environments without the need for wallets and mnemonics

Decentralized Identifiers
Enhancing Privacy: DIDs offer users greater control leading to improved privacy and trust

Decentralized Identifiers
Enhancing Privacy: DIDs offer users greater control leading to improved privacy and trust

Decentralized Identifiers
Enhancing Privacy: DIDs offer users greater control leading to improved privacy and trust

Decentralized Identifiers
Enhancing Privacy: DIDs offer users greater control leading to improved privacy and trust

PoS Blockchain Network
Energy efficient Proof of Stake Network designed from scratch for Digital ID management

PoS Blockchain Network
Energy efficient Proof of Stake Network designed from scratch for Digital ID management

PoS Blockchain Network
Energy efficient Proof of Stake Network designed from scratch for Digital ID management

PoS Blockchain Network
Energy efficient Proof of Stake Network designed from scratch for Digital ID management



TIME TO TAKE CONTROL
TIME TO TAKE CONTROL
Empowering humans to take control of personal data while ensuring businesses and regulators have access to verifiable data while maintaining privacy.

Simplifying Compliance for Businesses
Capture, Verify, Store & Manage user PII data in a simple, secure, compliant and privacy preserving manner.

Simplifying Compliance for Businesses
Capture, Verify, Store & Manage user PII data in a simple, secure, compliant and privacy preserving manner.

Simplifying Compliance for Businesses
Capture, Verify, Store & Manage user PII data in a simple, secure, compliant and privacy preserving manner.

Simplifying Compliance for Businesses
Capture, Verify, Store & Manage user PII data in a simple, secure, compliant and privacy preserving manner.

Data Ownership & Monetisation for Users
Rewarding Users for sharing their personal data while putting them in complete control of how and where their data is used and rewarding them in exchange

Data Ownership & Monetisation for Users
Rewarding Users for sharing their personal data while putting them in complete control of how and where their data is used and rewarding them in exchange

Data Ownership & Monetisation for Users
Rewarding Users for sharing their personal data while putting them in complete control of how and where their data is used and rewarding them in exchange

Data Ownership & Monetisation for Users
Rewarding Users for sharing their personal data while putting them in complete control of how and where their data is used and rewarding them in exchange

Mitigating Risk
Drastically reduce the risk of data hacks and breaches and compliance related penalties for financial and user data.

Mitigating Risk
Drastically reduce the risk of data hacks and breaches and compliance related penalties for financial and user data.

Mitigating Risk
Drastically reduce the risk of data hacks and breaches and compliance related penalties for financial and user data.

Mitigating Risk
Drastically reduce the risk of data hacks and breaches and compliance related penalties for financial and user data.
USE CASES
USE CASES
How Entity Protocol can help you
Identity For Artificial Intelligence
Create unique, verifiable identities for AI entities, enabling authentication, accountability, and trust in AI-human interactions.

On Chain Gaming
Engage in fully on-chain gaming experiences without concerns about bot interference.
Depin Infrastructure
Secure DePIN applications that handle mission-critical tasks, such as supply chain provenance and asset ownership.
Asset Tokenization (RWA)
Fast, and Lowcost on-chain verification of physical asset ownership, paving the way for permission-less minting of RWA tokens.

Authentication Verification
Secure verification process through biometrics that allows for authentication online and offline. Authenticate once and move freely.

Human DAOs
Ensure the integrity of one-person-one-vote election mechanisms, enabling the establishment of sophisticated governance frameworks such as electoral systems and governance structures.
Credential Verification
Relevant for Educational and Healthcare institutions Personal data, such as education and employment history, age and nationality can be shared and verified while maintaining user privacy.
Fairdrops Community
Ensures fairdrops remain viable by maintaining airdrops that are resistant to Sybil attacks, preventing fraudulent activities, and fostering inclusive participation from verified individuals.

Universal Basic Income (UBI)
Fair distribution of UBI by restricting recipients to wallets linked to verified unique humans, all without the need for traditional centralized identification.